The InfoSecBase ISMS Workbooks
ISMS Workbooks...
your InfoSecBase ISMS Toolkit includes several topic-specific workbooks to help you manage your ISMS documentation
From implementation, through certification and beyond

Asset Sub-Inventory Workbook
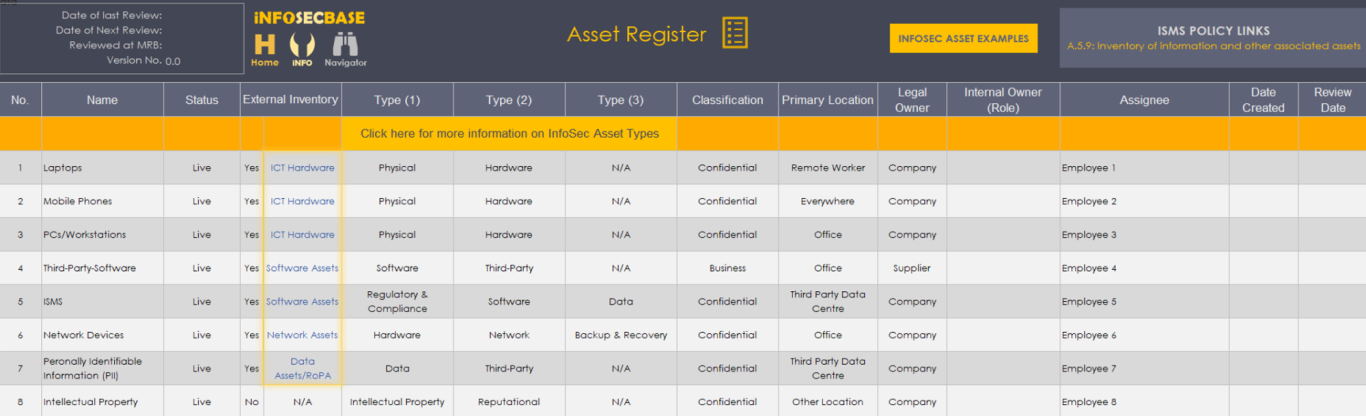
Your ISMS Platform contains your main high-level Asset Register template.
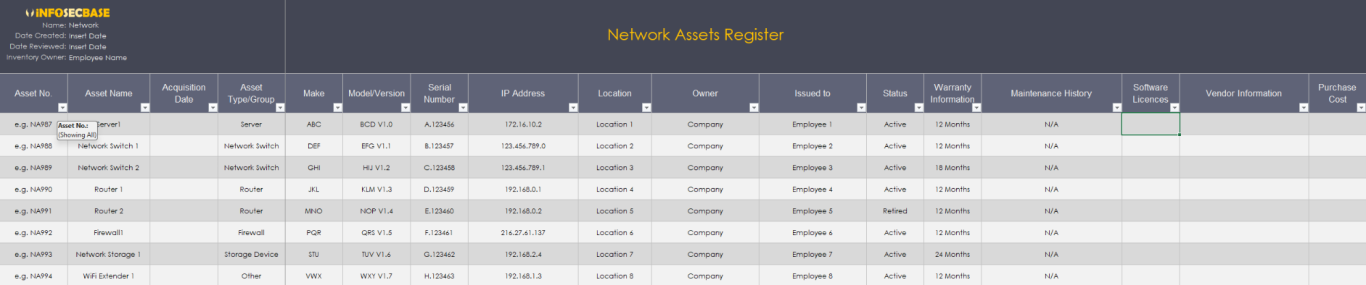
To prevent your main asset register becoming cluttered with every individual asset within your organisation, the InfoSecBase ISMS contains a separate workbook with individual registers, each designed specifically for each asset type, for your ICT Hardware Assets, Software Assets and Network Assets - Data Assets are recorded in the Record of Processing Activity (RoPA) and is located separately within the Data Management Workbook.
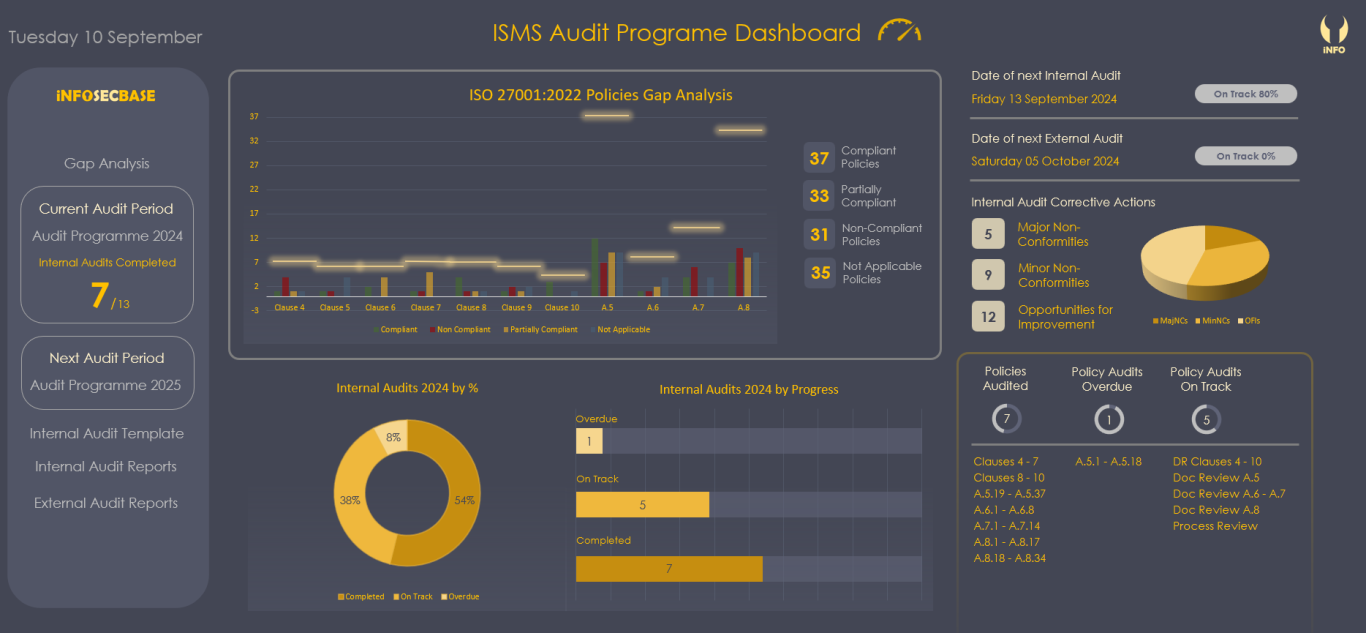
Audits Workbook
The Audits Workbook contains a Gap Analysis Audit, an Audit Planner and a set of suggested Internal Audit Templates, all of which can be accessed through the ISMS Audit Programme Dashboard which also shows charts and graphs of the current audit programme status.

Change Management and Planning Workbook
The Threat Intelligence (TI) Workbook is the ISMS area where you record all of your threat intelligence information. The workbook includes:
- A main register where you can log, categorise and manage your TI items.
- A tracker, where there's a visual representation of the current status of your TI items.
- A table that lists your TI sources, the purpose of contact, the frequency of contact and the type of source (strategic, tactical and/or operational).
- A set of templates to record your threat intelligence reports.
Corrective Actions and Improvements Workbook
The Corrective Actions and Improvements (CA&I) Workbook is the ISMS area where you record all of your corrective action and improvement information. The workbook includes:
- A main register where you can log, categorise and manage your CA&I items.
- A tracker, where there's a visual representation of the current status of your CA&I items.
- A set of templates to record your CA&I reports.
Data Management Workbook
The Data Management (DM) Workbook is the ISMS area where you record all of your data management information. The workbook includes:
- The Records of Processing Activity (RoPA); this is the register where you can record your data assets.
- A Data Retention Periods table, where you can determine the categories of data, the purpose of processing, record the periods that you retain data, the justification and the action taken at the end of the retention period.
- A Subject Access Request (SAR) Register, where you can log and track all requests.
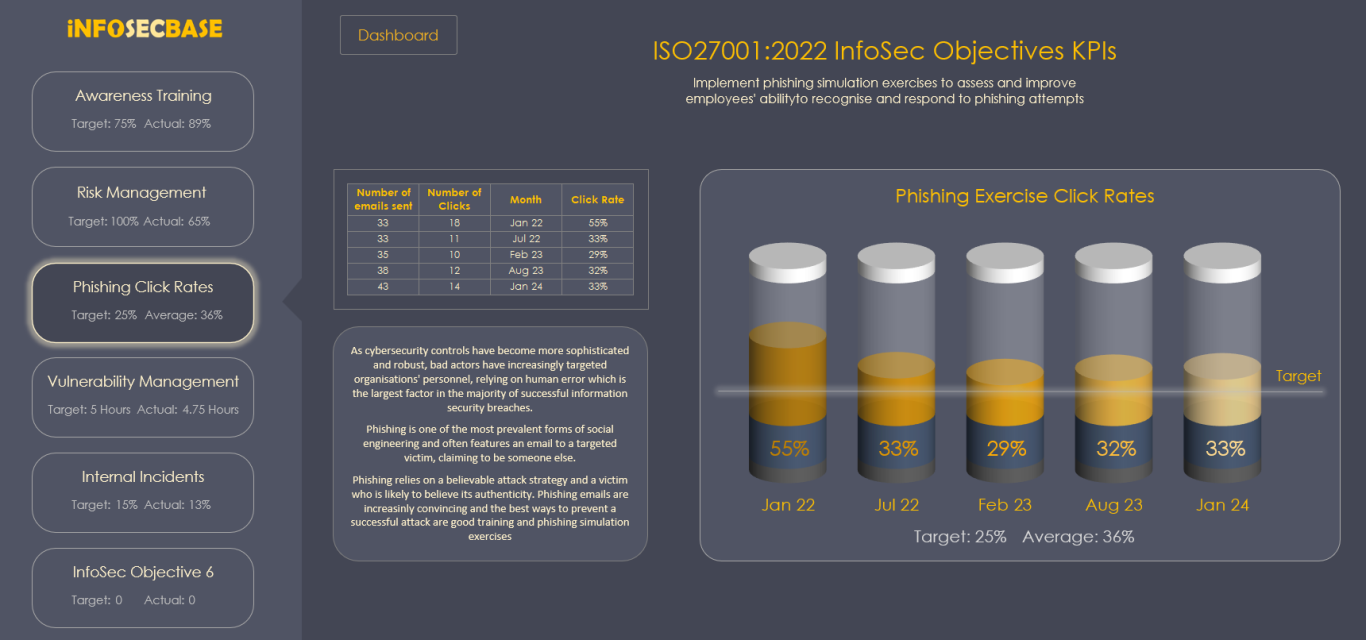
Key Performance Indicators Workbook
The Key Performance Indicators (KPI) Workbook is the ISMS area where you can record the performance and progress your Information Security Objectives in graphical format.
Management Review Meetings Workbook
The Management Review Team (MRT) Meetings Workbook is the ISMS area where you plan and record all of your MRT meetings.
Security Incident Management Workbook
The Security Incident Management (SIM) Workbook is the ISMS area where you record all of your SIM information. The workbook includes:
- A main register where you can log, categorise and manage your SIM items.
- A tracker, where there's a visual representation of the current status of your SIM items.
- A set of templates to record your SIM reports.
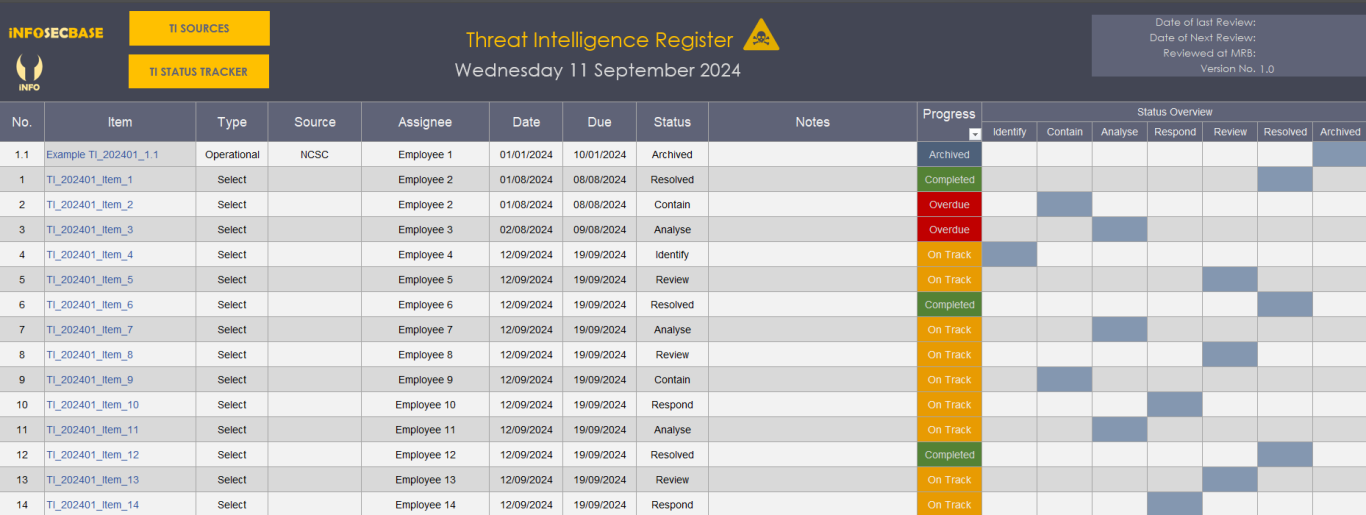
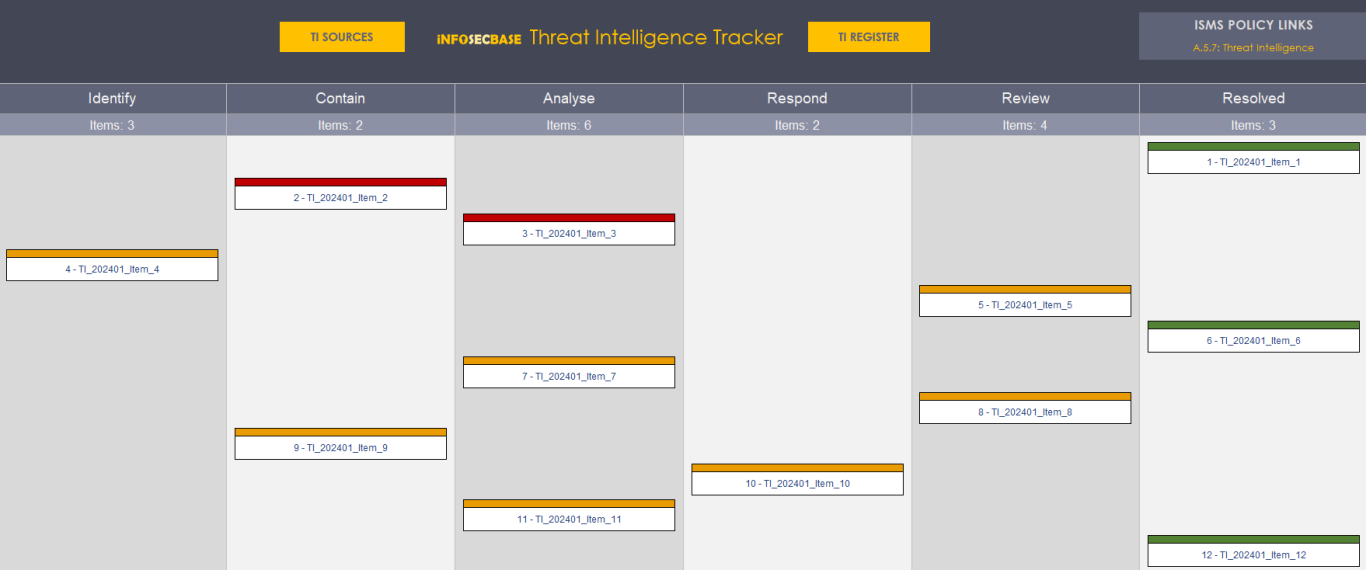
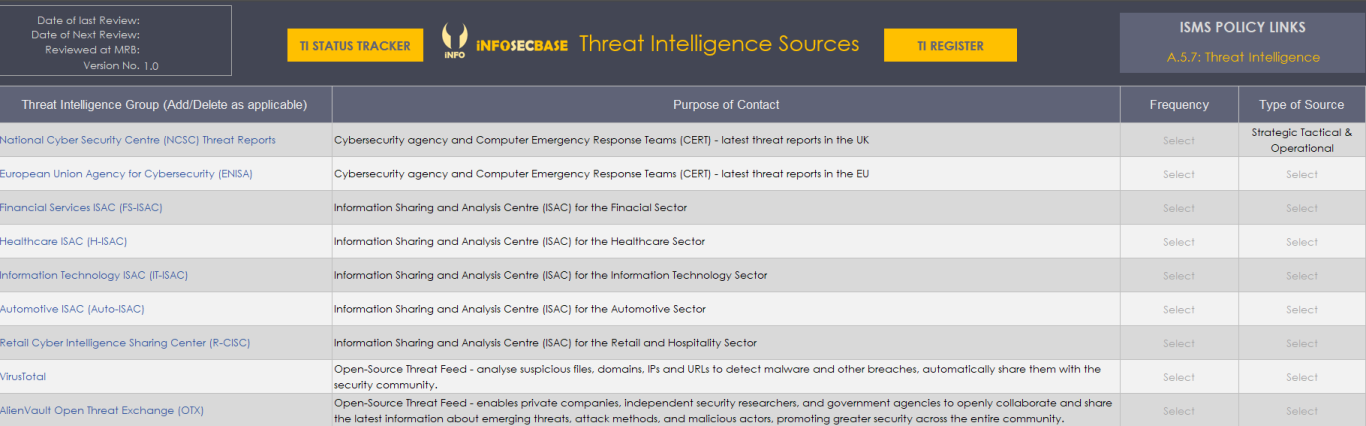
Threat Intelligence Workbook
The Threat Intelligence (TI) Workbook is the ISMS area where you record all of your threat intelligence information. The workbook includes:
- A main register where you can log, categorise and manage your TI items.
- A tracker, where there's a visual representation of the current status of your TI items.
- A table that lists your TI sources, the purpose of contact, the frequency of contact and the type of source (strategic, tactical and/or operational).
- A set of templates to record your threat intelligence reports.
“Technology trust is a good thing, but control is a better one.”
Stephane Nappo
We need your consent to load the translations
We use a third-party service to translate the website content that may collect data about your activity. Please review the details in the privacy policy and accept the service to view the translations.